In a groundbreaking revelation, a highly sophisticated security vulnerability has been discovered within the iPhone ecosystem, specifically through iMessage. This flaw, dubbed “Operation Triangulation,” has recently been disclosed in its entirety by security researchers at Kaspersky. Between 2019 and December 2022, an exceptionally advanced iMessage vulnerability came to light, labeled as “Operation Triangulation” by the Kaspersky security researchers who unearthed it. In this article, we delve into the intricate details of this unprecedented security breach.

The Intricacies of Operation Triangulation
Transitioning to the specifics, the researchers shared their findings on a flaw that persisted until the release of iOS 16.2 in December 2022. This flaw, as revealed by the investigation, led to a massive espionage campaign infiltrating the iPhones of thousands working in diplomatic missions and embassies in Russia.
Operation Triangulation involved a malicious attack through iMessage, requiring no action from the recipient. This complex assault facilitated the installation of malware via iMessage texts, enabling the attackers to implant fully-featured spyware on the devices. The researchers, Boris Larin, Leonid Bezvershenko, and Georgy Kucherin, express their astonishment, labeling this as “the most sophisticated attack chain witnessed to date.”
From Zero-Click to Zero-Day Vulnerability
According to the researchers, Operation Triangulation’s security vulnerability persisted until the release of iOS 16.2 in December 2022. The investigation outlines a widespread espionage campaign affecting iPhones belonging to individuals in diplomatic missions and embassies in Russia.
This attack chain, comparable in its sophistication to the notorious Pegasus zero-click iMessage vulnerability of previous years, has raised eyebrows in the cybersecurity community. Kaspersky researchers emphasize its severity, with the attackers exploiting four undisclosed zero-day vulnerabilities, targeting devices with zero-click spyware.
Unraveling the Mystery
As the researchers meticulously reverse-engineer every aspect of this attack chain, they plan to release more in-depth articles in 2024, detailing each security vulnerability and its utilization. However, intriguingly, the research team has not fully unraveled all the security vulnerability details, particularly regarding how the attackers were aware of the undisclosed hardware feature.
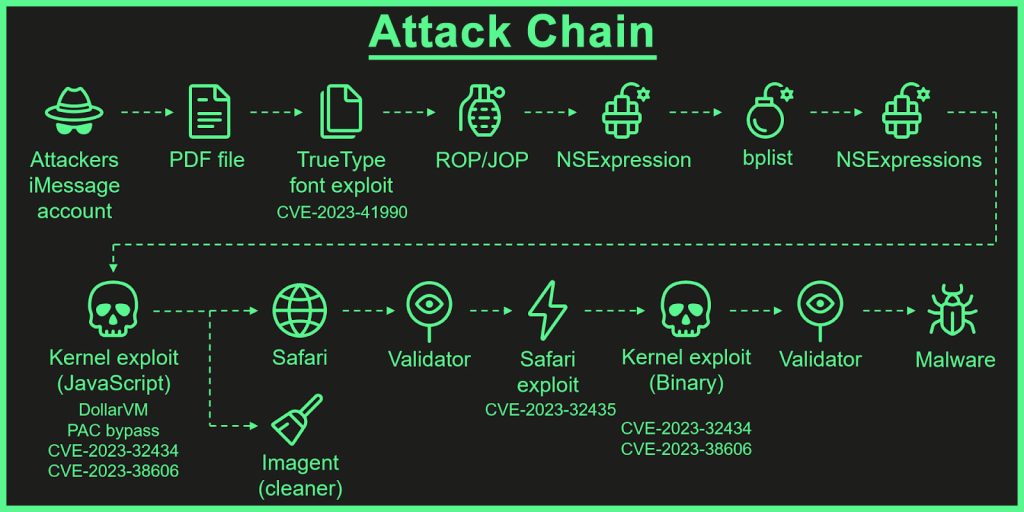
One of the most intriguing aspects of this incident is the targeting of a previously unknown hardware feature, proving to be of significant importance. This zero-day vulnerability in the hardware allowed the attackers to bypass advanced hardware-based memory protections designed to preserve the system’s integrity.
Possible Culprits and Allegations
While the research sheds light on the attack’s magnitude, attributing it to unknown actors, the attackers’ origin remains unclear. Russian authorities allege the involvement of the United States National Security Agency (NSA) in infecting thousands of iPhones in diplomatic missions, particularly those representing NATO countries, former Soviet nations, Israel, and China.
On the flip side, Apple, in collaboration with the NSA, has categorically denied involvement in this campaign. Kaspersky researchers, while presenting their findings, emphasize their lack of evidence confirming the involvement of either the NSA or Apple in the alleged campaign.
In summary
Operation Triangulation stands as a testament to the evolving landscape of cybersecurity threats, showcasing a level of sophistication unparalleled in previous attacks. As the cybersecurity community grapples with the aftermath of this revelation, questions linger regarding the true extent of the vulnerability and the identities of those behind this audacious operation.




